Essentials stuff
A. OVERVIEW
-
This handbook is split into two parts. The first part is the step by step guide to data handling in your current workplace. The second part includes the extended rationale and explanations for the importance of data security in the office.
-
All transcription team members are required to read the Data Handling Handbook and sign both the Data Handling and Non Disclosure Agreement forms.
-
Transcription team members are also required to familiarize themselves with relevant parts of NTU’s Research Data Management Policies as well as NTU’s official Personal Data protection Statement.
-
Non transcription team members will not have access to any audio files, unless they have been released for public archiving. People who have not read or signed both required forms will not be allowed to handle the audio files.
-
Promotion to occupational positions of increased levels of security clearance is always possible.
B. DATA HANDLING PROCEDURE
-
Audio files will be stored on a secured server. When transcribing the ELAN file, direct the program towards the audio file on the server. If working remotely, audio files should still only be accessed via server. Audio files should never be downloaded onto your personal computer without explicit permissions to do so.
-
Close all programs when you leave. This is to ensure that no participants’ privacy can be breached by anyone looking at your screen while you are transcribing.
-
Do not share your work passwords and login accounts with others. Do not use the same password for your work account with any other accounts. Log out of shared drives when you are not working.
-
In cases where a thumb drive is being used, the thumb drive should never leave the LIFESPAN office, and the audio data should not be copied to the computer. The thumb drive should be stored in a locked location when not in use.
-
The ELAN files will be transferred to the server as well. Once upload on the server is verified, ELAN file should be deleted from the drive in question. ELAN files will not be saved on any personal computer.
-
If it is not possible to access the server, audio files and ELAN files will be saved only on a secured portable storage device (thumb drive, memory card, portable HDD, etc.). Special permissions will need to be obtained before you do so.
-
If using the harddrive, save the ELAN file on the harddrive before commencing. At no point should anything be copied or downloaded onto their personal computers.
-
No files will be downloaded on any personal computer.
-
No copies will be made unless for an activity that has been ethically approved by the PI.
-
Authorized task managers may move the copies if required, without accessing the contents of the files.
C. HIERARCHY OF DATA ACCESS
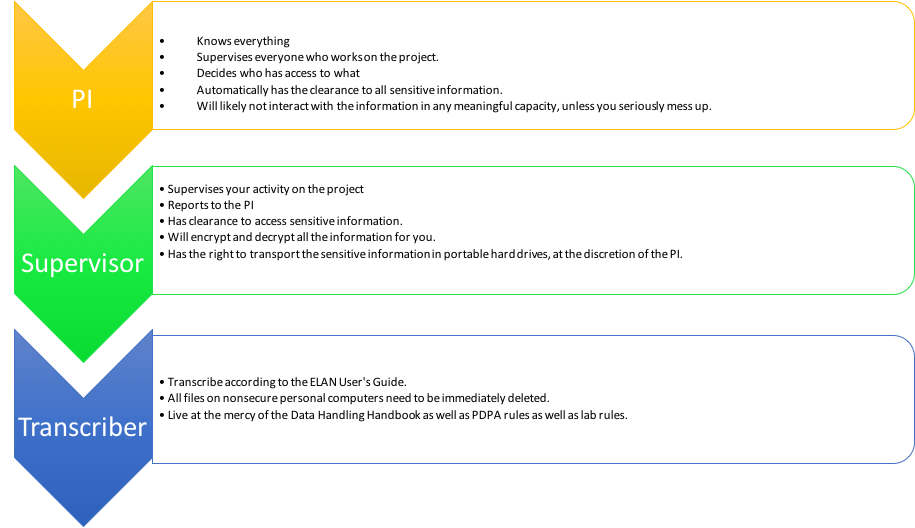
D. CONFIDENTIALITY GUIDELINES
• All informed consent given by participants must be obtained in writing accompanied with a comprehensive set of purposes for collection, use and disclosure of the personal data.
• All personal data must be kept accurate and up-to-date and must not be kept longer than necessary.
• Every employee must take precautionary measures to ensure that the personal data is being kept secure from misuse and unauthorized access. This includes adhering to the stated Data Handling Procedure and Confidentiality Agreement.
• Every employee must take note of data transfer and data storage guidelines included in the stated Data Handling Procedure.
• Every employee will maintain confidentiality with regards to all content on the audio recordings, with the only exceptions being other members of the transcription team who have received similar or more training in data handling.
• No sharing or exchanging of personal data is allowed between organisations unless written consent from the individual has been obtained.
• Use “BCC” field when mass mailing to members of the public to mask other recipients email address. When in doubt, check with your supervisors.
Taken from: PDPA Guidelines for Student Organisations (NTU)
Mandatory Reporting Guidelines
The only exception that exists to the confidentiality rule is when any employee has reasonable cause to suspect that a Minor involved in the recording has been the victim of child abuse. In this case, said employee shall immediately report the suspected abuse consistent with this policy. This is a mandatory reporting obligation.
What Must Be Reported
You must report child abuse you have reasonable cause to suspect. Child abuse, according to the CPSL, means intentionally, knowingly or recklessly doing any of the following
- Causing bodily injury to a child through any recent act or failure to act.
- Fabricating, feigning or intentionally exaggerating or inducing a medical symptom or disease which results in a potentially harmful medical evaluation or treatment to the child through any recent act.
- Causing or substantially contributing to serious mental injury to a child through any act or failure to act or a series of such acts or failures to act.
- Causing sexual abuse or exploitation of a child through any act or failure to act.
- Creating a reasonable likelihood of bodily injury to a child through any recent act or failure to act.
- Causing serious physical neglect of a child.
- Engaging in any of the following recent acts:
- Kicking, biting, throwing, burning, stabbing or cutting a child in a manner that endangers the child.
- Unreasonably restraining or confining a child, based on consideration of the method, location or the duration of the restraint or confinement.
- Forcefully shaking a child under one year of age.
- Forcefully slapping or otherwise striking a child under one year of age.
- Interfering with the breathing of a child.
- Causing the death of the child through any act or failure to act.
- Leaving a child unsupervised with an individual, other than the child’s parent, who the actor knows or reasonably should have known
- is required to register as a Tier II or III sexual offender;
- has been determined to be a sexually violent predator; or
- has been determined to be a sexually violent delinquent child.
“Recent” is defined as any act of child abuse committed within the previous two years. Sexual abuse, serious mental injury, serious physical neglect and deaths have no time limit.
How to Make a Report
Notify your supervisor immediately.
E. KEEPING DATA SECURE IN THE WORKPLACE
In the lab, you must ensure that data is always closely monitored and secured. This means that if you are working with hard copies of data (e.g., paper forms, individual participant results), you must ensure that they are safely locked away in a secure location whenever you have to leave from their line of sight.
As a member of the transcription team, you always have a responsibility to maintain the security of sensitive information. Please bear in mind, that not all members of your lab are authorized to access certain kinds of protected data, and may not have been trained to do so. As such, when you leave your desk, maybe for a quick break, you should always make sure to lock your computer screens before you leave to prevent any sensitive information from being exposed to non-authorized individuals. On the flip side, leave your laptop screen on, be prepared to find the lid closed when you return.
That said, it is also your responsibility to help other members of your lab maintain the same level of oversight in their work. For example, if you see that your fellow lab member has left hard copy forms unattended on your desk, you should put them in a secure location and remind them when you next see them.
If you are holding onto a portable device that contains protected information, you should also take care to lock it in a safe place when you leave the room, or to keep it on your person at all times. If possible, avoid storing any confidential data or personal details on portable storage devices and access the local network using only secure methods. If absolutely necessary to use a portable storage device, set access codes to your portable devices and always use strong passwords or access codes.
As a reminder, the criteria for a strong password includes:
- 8-16 characters
- at least one upper case letter
- at least one lower case letter
- at least one number
- at least one special symbol %$ etc.
Do check out the NTU guideline on strong passwords for further tips:
F. WHAT HAPPENS IN THE SITUATION OF A DATA BREACH
Firstly, no matter what kind of data breach, your main role is to inform your supervisor immediately, before taking any action. Your supervisor is better equipped than you are to handle such situations. This section is mainly to tell you what happens in case of a data breach.
There are different consequences depending on the type and security of data breach. This section will deal with commonly encountered types of data breach.
Losing a portable storage device
- Check that the device is definitely not within secure lab confines.
- Check whether another team member has taken custody of the storage device when they noticed it was unsecured.
- Check that the device cannot be found in other places known to you.
- Tell your supervisor. Be clear when you think it happened, and what data could be compromised.
- Make a report to relevant ‘lost and found’ services if applicable.
Revealing identifiable information to the wrong email addresses (i.e. contact a wrong parent
- There are a few ways this might happen. The most common is either a) sending an email to the wrong parent on your contact list or b) sending an email blast without ensuring that all recipient emails are kept confidential.
- Note that this is a breach of PDPA laws, which will be covered in more detail in the next section of this handbook.
- Your job is to be cautious when sending emails.
- Make sure you remember to use the BCC function in all circumstances.
- Always sign off using “[Your Name] for BLIP Lab” at the end of your emails.
- In a situation where a breach has occurred, let your supervisor know immediately before trying to handle the situation yourself.
Finding that there has been a breach in the secure network (i.e. a hacker)
- Note down what makes you think so.
- Let your supervisor know immediately. If they are not available, inform another senior team member immediately. In our team Dr Le Tuan Anh is the person in our team who is best qualified to help us find out if a breach of this kind has occurred, and what steps we should take next. For example, our senior team members may decide to disconnect the server from network, but this decision should only be taken by lab members with Admin privileges.
Overhearing a colleague speaking to a non-authorized person about sensitive information gleaned from the data
- Immediately inform your colleague that you think the information they are sharing is protected by the team’s privacy policy.
- Check with your colleague whether they think there are legitimate reasons for sharing with this person.
- Evaluate whether you think the information is of such a sensitive nature that further action needs to be taken immediately, in which case inform your supervisor or a senior lab member immediately.
- Discuss the case with your supervisor when possible and consider whether it would be a suitable topic for discussion at a future team meeting.
Child protection is our number one priority. In all of the above cases, sensitive information could fall into the hands of malicious actors, including those who may have the intention to harm children. This is a situation you are obligated to prevent at all cost.